Back
Platform
The integrated signal for extended detection and response (XDR). Detect – Prioritize – Investigate – Respond
Our AI
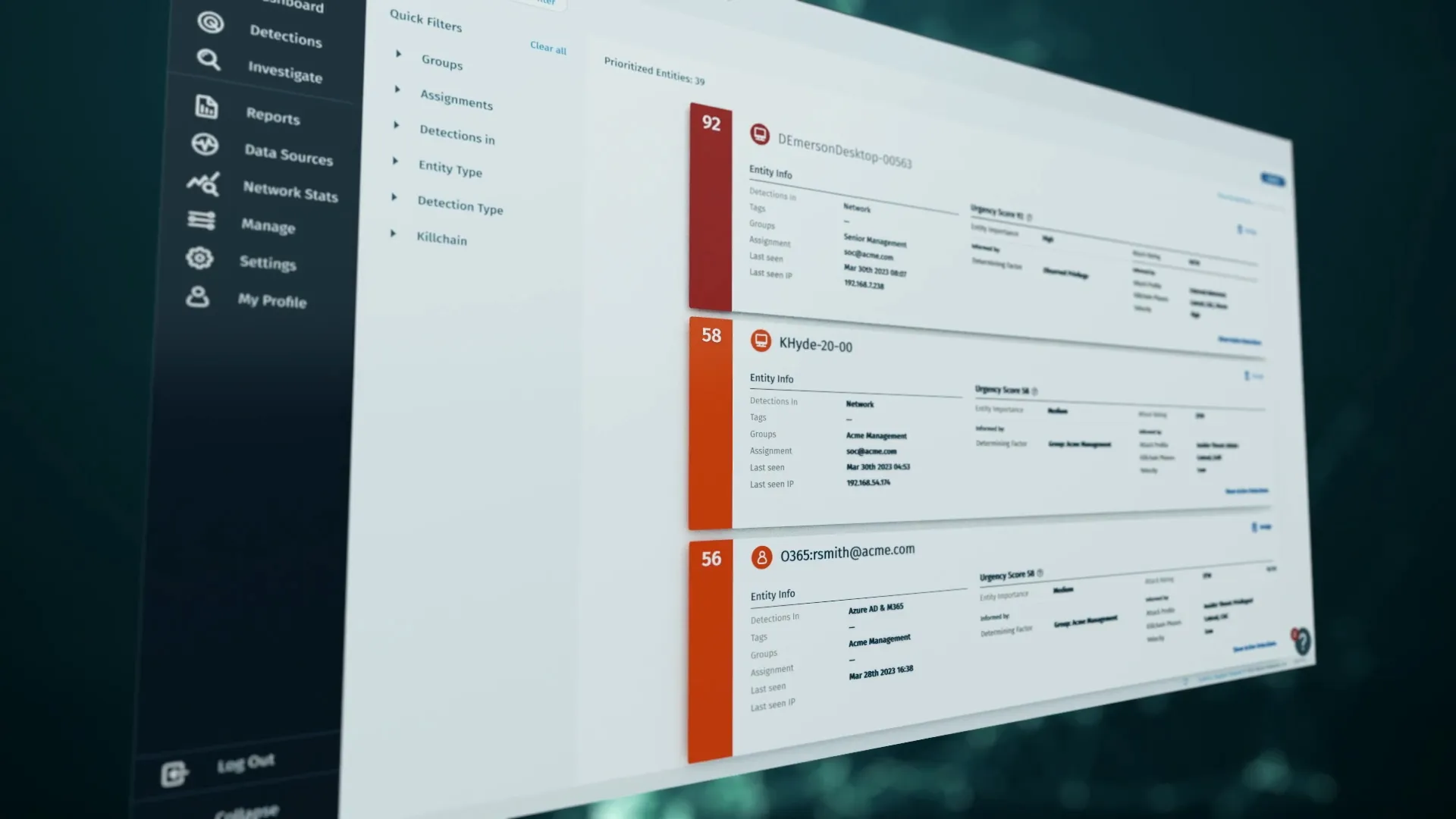
Arm your security analysts with intel to stop attacks fast. Attack Signal Intelligence analyzes in real-time to show where you’re compromised right now.
Use Cases
Attack Types
Emerging Attack Methods
Industries
Back / Platform
Attack Types
Emerging Attack Methods
Back
Customers
Support Hub
Professional Services
Research
Expert insights from Vectra AI data scientists, product engineers and security researchers empower your SOC analysts to make faster, smarter decisions.
Attack Labs
Join our security researchers, data scientists, and analysts as we share 11+ years of security-AI research and expertise with the global cybersecurity community.
Resources
Product in action
Find a Partner
Become a Partner